BIOCTL - External Disk Encryption on OpenBSD
July 17, 2020
As a Criminal Defense Detective and Contractor on Federal CJA-Cases, I have chain-of-custody of uncovered evidence, investigative reports, work-products, affidavits, statements, audio-files, video-files, photographs, etc.
Working on these criminal investigations requires proper and efficient case management as well as compliance to Federal, State and Local laws, regulations and standards governing the handling of confidential files, records, client's data and evidence gathered during the course of an investigation.
Encryption becomes absolutely necessary for the confidentiality and integrity of all digital evidenciary items. The proper cryptographic implementation should keep evidence available for examination and analysis without the risk of spoliation.
While Federal Government Agencies and the U.S Military are very well structured and equipped with great cryptographic protocols and standards, implementation of a robust cryptographic infra-structure and good training remains inexistent on various State-Level and Local-Level Agencies.
In the middle of 2020, the great majority of legal professionals: district attorneys, public defenders, law enforcement detectives, criminal defense detectives and investigators from the private sector, still go about their usual business without having a clue of cryptography, its applicabilities, its operations and its executions within the realm of investigations.
The same cannot be said about the various U.S Federal Agencies and the U.S Military, all of which must strictly comply to cryptographic standards specified in the Homeland Security Presidential Directive (HSPD12) that attempts to give a guarantee of data/evidence confidentiality, preservation, integrity, and availability, as well as the authenticity of their ID cards, digital signatures, etc.
In my 15 years of experience in the realm of law enforcement work and criminal investigations, I can say how easy it is for the majority of local prosecutorial agencies to cause evidence spoliation during the course of their investigation for not adhering to sound cryptographic implementation and protocols. Worse can be said about public defender offices across America and private attorneys nationwide who are mostly ignorant about cryptographic equipment, encryption protocols, Federal standards and laws.
Private Attorneys from both Nevada and Massachusetts cannot be that ignorant about encryption though. Both Nevada and Massachusetts have legally mandated encryption as part of their consumer protection regulations.
Massachusetts information security law, M.G.L. c. 93H, applies to “persons who own, license, store or maintain personal information about a resident of the Commonwealth of Massachusetts.” The law applies to all private businesses including lawyers and law firms and requires that an organization have a written security plan that includes “to the extent technically feasible, . . . encryption of all transmitted records and files containing personal information that will travel across public networks, and encryption of all data containing personal information to be transmitted wirelessly.” The organizational program also must include encryption of all personal information stored on laptops or other portable devices.” Covered “personal information” includes Social Security numbers, driver’s license numbers, state- issued identification card numbers, financial account numbers and credit card numbers. This law has been enforced against out-of-state businesses having sufficient minimum contacts with the Commonwealth of Massachusetts.
In July 2014, the Attorney General, enforced a civil penalty of $150,000 against the Women & Infants Hospital of Rhode Island (“WIH”) to resolve allegations that it lost unencrypted data. This legal action demonstrates that the Massachusetts Attorney General is aggressively engaged in enforcing both Federal and Massachusetts information security law against out-of-state entities who insecurely store the personal data of Massachusetts residents.
In addition to state-mandated legal schema, attorneys have a clear ethical responsibility to protect client information. Rule 1.6 - Confidentiality of Information - of the Model Rules of Professional Responsibility by the American Bar Association (ABA) states that, “A lawyer shall make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.” As the comments to the section reads, the “fundamental principle in the client-lawyer relationship is that, in the absence of the client’s informed consent, the lawyer must not reveal information relating to the representation.”
As an instructor in the area of cryptography applied to investigations, I teach to members of law enforcement, the military and legal professionals from the private sector on the usage of various Unix-based and GNU/Linux-based cryptographic tools.
In this article, I will cover encryption of an external device pertaining to safeguarding evidence from unauthorized access. I will cover disk and block encryption using BIOCTL/softraid0 via OpenBSD, which is the most secure monolithic operating system in the world, not my opinion - it is a fact.
Requirements
- A computer running OpenBSD.
- An external device, such as: hdd, ssd or usb-flashdrive.
Optional
- You can create an encrypted container within your local hard drive, which can be mounted and unmounted as a "virtual" device. I also highly recommend that you install OpenBSD with Full Disk Encryption (FDE) in your main drive.
Background and Overview of BIOCTL/softraid0
OpenBSD's disk encryption has been implemented differently than on Linux or FreeBSD.
Linux uses dm-crypt or LUKS/cryptsetup and FreeBSD uses geli or gbde. On OpenBSD 5.7 onwards, the user can utilize softraid0 driver to acquire disk or block encryption. The BIOCTL command first appeared on OpenBSD 3.8; this article is being generated on OpenBSD 6.7.
I cannot recommend Microsoft Windows, MacOS and/or Google Applications; they pretend to offer you "digital security", but they never give you any freedom - instead, they own your system and they conduct surveillance of all your digital actions. Big Tech cannot be trusted with your digital life and much less with your cryptographic operations. Windows, Apple and Google offer you a false sense of security, which is worse than no security at all. I normally do not recommend the use of Operating Systems that have implemented Non-Disclosure Agreements (NDAs) either, which is the case of FreeBSD and some flavors of Linux - these systems become untrustworthy for cryptographic operations - one can never completely know what parts of the system or what some of the drivers may be doing under the hood - the possibility for backdoors and rootkits are enormous; on the other hand, NDAs are NEVER acceptable on OpenBSD (Source: https://www.openbsd.org/goals.html). I have to commend Theo de Raadt for his strong and uncompromising stance on security, accountability, transparency, and excellence on OpenBSD's source-code quality and minimalistic design. Proprietary encryption tools are not advisable either since you cannot audit them. In contrast, the OpenBSD project produces a FREE, multi-platform 4.4BSD-based UNIX-like full operating system with all the bells and whistles by default.
OpenBSD efforts to emphasize portability, minimalism, standardization, correctness, proactive security, mitigations, and integrated cryptography have set them apart from any other Operating System Project currently running on a monolithic-kernel design. Freedom is not for free, and the OpenBSD project has certainly paid a big price for it. OpenBSD is one of the greatest technological gifts to the world.
Back to the subject, the softraid subsystem works by emulating a scsibus with sd devices made by combining a number of OpenBSD disklabel partitions into a virtual disk with the desired RAID level. This virtual disk is treated as any other disk, first partioned with fdisk and then disklabels are created as usual. Note that only RAID0, RAID1, RAID5 and CRYPTO are fully supported at the moment this article is being published.
BIOCTL is a RAID management interface with CRYPTO discipline for disk and block encryption, also known as a Cryptographic Softraid Volume/Container.
Softraid is a RAID software driver.
Steps and Commands
1 - List/Name all the disks/volumes currently present on your system & identify which one is your external disk:
1.1 - Run the commands below before plugging your external drive into the machine to identify all your other drives first.
$ dmesg | egrep '^([cswf]d). '
$ sysctl -a | grep -i disk
1.2 - Plug your external device & run the commands above again to identify which new device was added and its device ID/name.
WARNING: Be extremely careful to correctly identify your external drive, or else you can completely wipe out all your data whether they are mounted or not. On this example we assume that the external disk or usb drive is "sd3". All the following commands have to be executed with root privileges.
2 - After having IDed your external drive, overwrite it with random data. Depending on the size of your device, this process can take hours:
# dd if=/dev/urandom of=/dev/rsd3c bs=1m
3 - Partition the disk (the -i flag reinitializes the partition table and -y answers yes to all prompts)
# fdisk -iy sd3
4 - Create the desired RAID-type partition 'a' with disklabel. This step involves typing into an interactive prompt:
# disklabel -E sd3
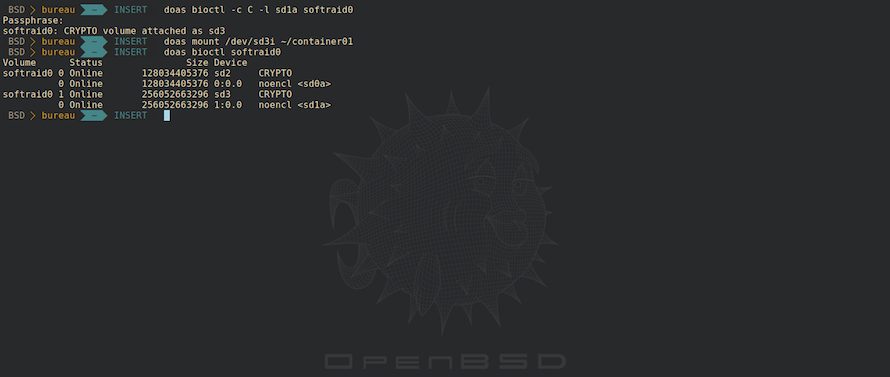
5 - You can now encrypt the drive/volume via BIOCTL. The parameter -c specifies the RAID level for our volume, C is a CRYPTO-type volume. The -r flag specifies the number of encrytion key generation rounds. The default number of KDF iterations is set to 16. In our case, we use the -r flag to raise the number of rounds to 8192. A larger number of iterations offers increased resistance against passphrase guessing attacks; however, it can take considerably more time every time you need to decrypt the drive. The -l flag specifies the chunk device to use. Softraid0 is the softraid device/driver. The default algorithm used by BIOCTL is AES-XTS-256, which is a standard one in 2020. Command below will ask you to set a passphrase. Please, choose a random passphrase of at least 46 characters (lower, upper, numbers, special characters or an aglomeration of at least 16 different words separated by spaces):
# bioctl -c C -r 8192 -l sd3a softraid0
NOTE: Softraid0 will display how the CRYPTO volume has been attached as. In our case 'sd4', which is a pseudo-partition.
6 - We can now zero the first megabyte of the new pseudo-partition. We will then initialize the device and create an 'i" partition, usually reserved to partitions outside the disklabel, like MS-DOS:
# dd if=/dev/zero of=/dev/rsd4c bs=1m count=1
6.1 - Partition the new volume:
# fdisk -iy sd4
6.2 - Use disklabel to create a type 'i' partition with a BSD File System (UFS) Native (FFS2). It's an interactive prompt:
# disklabel -E sd4
7 - Create a filesystem on the pseudo-device with newfs:
# newfs sd4i
8 - Mount the new pseudo-device on an empty directory. In our case container01.
# mount /dev/sd4i ~/container01
9 - Access the mounted encrypted container/volume. You can now transfer files, reports, documents and all uncovered evidence from your investigation/case into it:
# cp criminal-case-1234567-2020.tar.xz.bin ~/container01
9.1 - After this intial mount, you can change the permissions of your encrypted drive to match your local setup. In my case, I could do the following:
$ doas chown -R det001:wheel ~/container01
10 - Unmount the newly encrypted container & detach the encrypted device:
$ doas umount ~/container01
$ doas bioctl -d sd4
Daily Usage of your Encrypted Driver/Container:
$ doas -c C -l sd3a softraid0
$ doas mount /dev/sd4i ~/container01
$ df -h
NOTE: Remember to always unmount and detach before removing the encrypted drive or before turning off your workstation (Step #10)
Final Remarks:
Departmental policies and procedures must be checked first, and an approval from your department is necessary before you can engage in any type of encryption involving governmental records. If you are a private attorney or private investigator, check your state and local laws first; if none exist, you can create your own internal policy and highly benefit from encryption.
Whether you are a law-enforcement officer or a criminal defense investigator, federal agent, military-personnel, civil-service and/or private-sector legal professional, or a concerned citizen that values privacy, confidentiality and security, OpenBSD is a viable and solid option. Departmental policies and procedures must be checked first, and an approval from your department is necessary before you can engage in any type of encryption involving governmental records. If you are a private attorney or private investigator, check your state and local laws first; if none exist, you can create your own internal policy and benefit from encryption regardless.
I have given workshops and training regarding Cryptography Applied to Investigations to various professionals, including: Police Precinct Commanders, Homicide Detectives, Forensic Investigators, Bomb Squad Supervisors, Military Personnel, and Defense Attorneys.
For more information regarding Cryptography Applied to Investigations, Operating Systems that I recommend or to attend a workshop/seminar check: Cyber SWAT